How it works
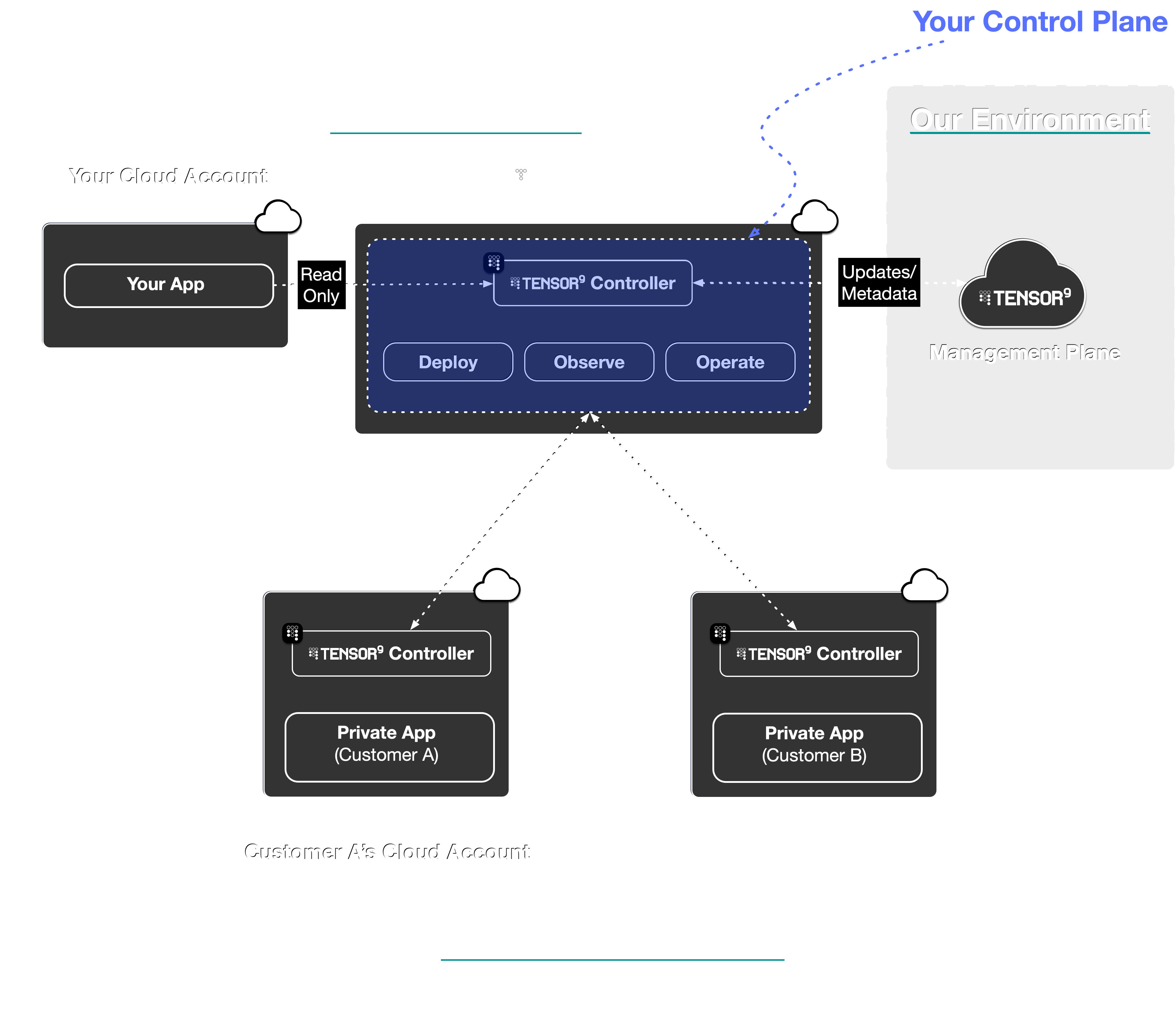
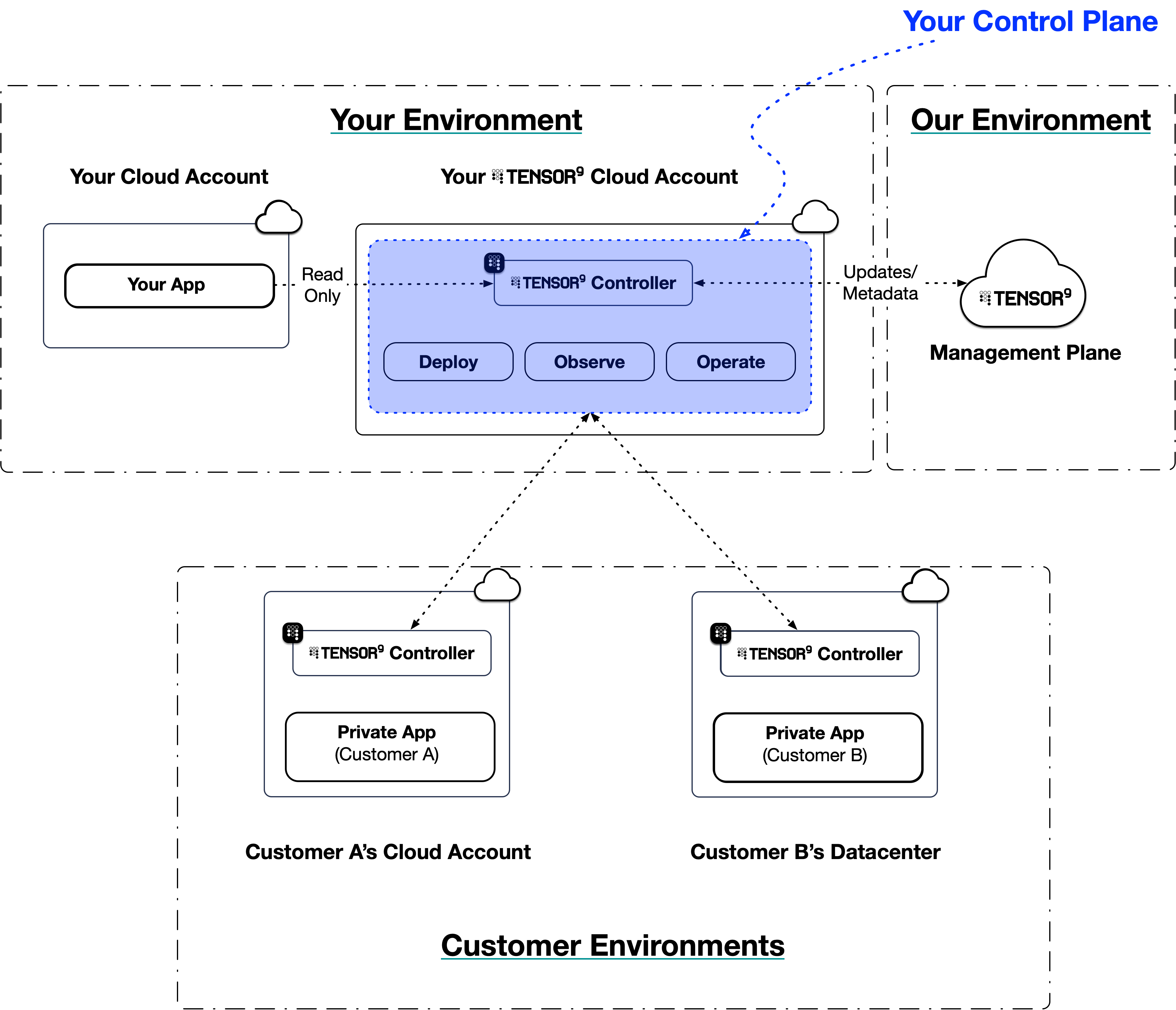
Once installed, your control plane acts as the central authority for managing your software distribution. It runs within your cloud account, using read-only IAM roles to interact with your origin stack’s infrastructure-as-code, artifacts, and secrets. Its responsibilities are divided into three main areas: deployments, observability, and operations.Deployments: From origin stack to appliance
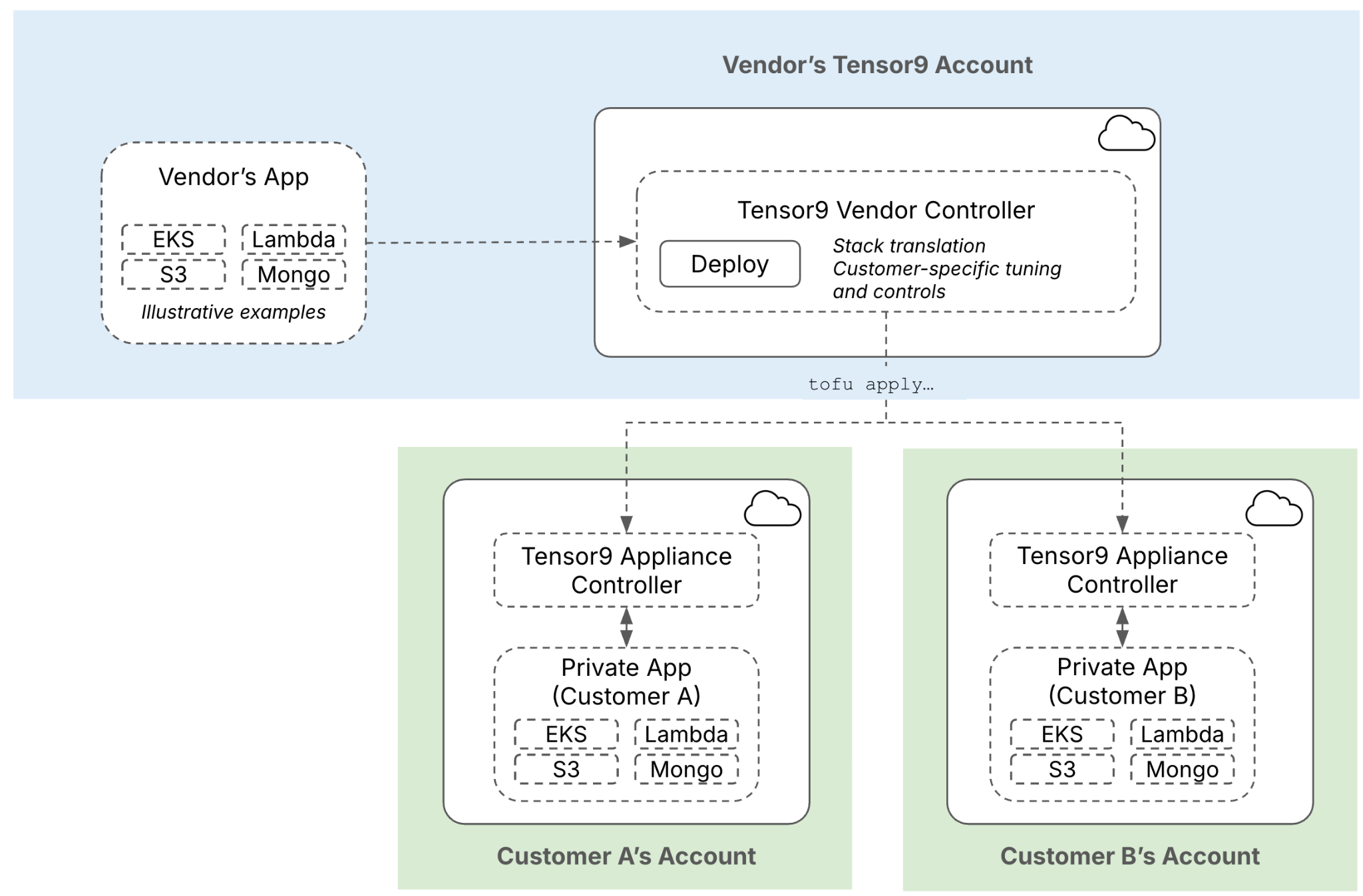
Your control plane automates the process of compiling your app into customer-specific appliances. This process begins with your origin stack. An origin stack is the blueprint for your application - it can be a Terraform workspace, a Docker image, or a CloudFormation template. When you publish a new version of your origin stack and create a release, your control plane “compiles” it into a deployment stack. This compilation step involves:- Validation: Your control plane inspects the origin stack to ensure it’s well-formed and meets Tensor9 requirements.
- Porting: It translates cloud-specific resources in your origin stack to their equivalents in the target customer’s environment, based on the appliance’s form factor. For example, if your origin stack uses AWS RDS for its database, but the customer’s appliance is set to run on Google Cloud, your control plane will replace RDS with Cloud SQL during compilation.
- Observability: It prepares the stack to be observed when deployed within an appliance by configuring the routing for logs, metrics, and traces.
- Packaging: The result of this compilation process is a deployment stack. This is a self-contained, deployable infrastructure-as-code artifact you deploy in your own environment (e.g.
terraform applyortofu apply) that deploys your application into a specific customer’s appliance.
Observability: centralized logs, metrics, and traces
Your control plane handles observability for all deployed appliances by ensuring the instrumentation your application already has continues to function. Tensor9 does not add new agents or require code changes; instead, it configures the routing needed for the telemetry your application is already configured to produce. The appliance runtime captures the telemetry data that your software and its underlying infrastructure generates, including:- Logs: App logs that your software writes to standard output.
- Metrics: Custom metrics your software produces, and system metrics your infrastructure produces (e.g. k8s node CPU utilization, storage bucket size).
- Traces: Distributed traces your software produces.
Integrating with existing observability
Tensor9 works with your existing observability setup. It configures the appliance environment so that your application’s existing telemetry is sent to its original destination. For example, consider an origin stack defined in Terraform. Tensor9 automatically injects a uniqueinstance_id variable into your configuration for each appliance.
instance_id variable in the log group name, you ensure that each appliance creates a distinct log group. When an appliance is deployed, the logs from my-function will be sent to a unique log group /aws/lambda/my-function/appliance-xyz-123. This allows you to observe each customer environment in isolation while using the same origin stack for all deployments. Your existing dashboards and analysis tools can then be configured to monitor these per-appliance log groups.

Operations: secure remote management
Your control plane provides operational endpoints that allow you to perform day-2 operations on your appliances. This provides an auditable method for remote management. When an appliance is created, it establishes a secure, outbound-only tunnel to your control plane. This tunnel allows you to use thetensor9 CLI to:
- Access a remote shell inside an appliance for debugging.
- Run specific, one-off commands or scripts (e.g., database migrations, data backfills).
- Securely manage secrets and environment variables for a specific appliance.
- Restart services or trigger other state changes.